Unveiling The Hidden Security Weakness In VNC: What You Need To Know
Ever wondered why your remote connections might be vulnerable? Security weakness in VNC is a growing concern that affects millions of users worldwide. It’s not just about convenience anymore—it’s about staying safe while working remotely.
Let’s face it, Virtual Network Computing (VNC) has been a lifesaver for many businesses and individuals who rely on remote access to get things done. But what happens when the tool you trust the most turns into a potential security risk? That’s right—we’re diving deep into the world of VNC security flaws and uncovering the hidden dangers lurking in the shadows.
In this article, we’ll explore the security weakness in VNC, how it impacts your data, and most importantly, how you can protect yourself. So grab a coffee, sit back, and let’s get started on this journey to secure your digital connections.
Read also:Misty Roberts Clanton The Story Of A Remarkable Woman Who Inspires Many
Understanding VNC: The Basics
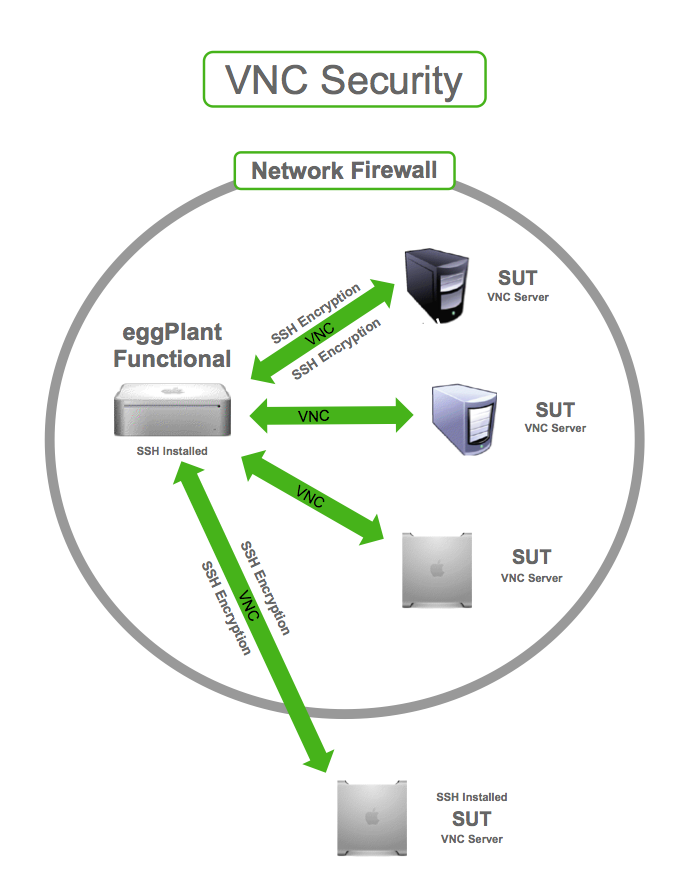
VNC, short for Virtual Network Computing, is a system that allows users to remotely control another computer. It’s like having a virtual window into someone else’s desktop, giving you the ability to access files, applications, and settings from anywhere in the world. Sounds pretty cool, right? But here’s the kicker: not all VNC setups are created equal, and that’s where the security weakness in VNC comes into play.
How Does VNC Work?
VNC works by transmitting keyboard and mouse input from one computer to another over a network connection. The remote computer sends back screen updates, allowing you to interact with it as if you were sitting right in front of it. However, the way this data is transmitted can sometimes leave room for vulnerabilities.
- VNC uses a client-server model where the server is the computer being controlled, and the client is the computer doing the controlling.
- Data is typically sent over TCP/IP, which can be intercepted if not properly encrypted.
- Authentication methods vary, but some older versions of VNC use weak password protection, making them easy targets for hackers.
Common Security Weakness in VNC
Now that we’ve covered the basics, let’s talk about the elephant in the room: the security weakness in VNC. There are several common vulnerabilities that you should be aware of if you’re using this technology.
Poor Password Protection
One of the biggest issues with VNC is the use of weak passwords. Many users opt for simple, easy-to-remember passwords, which makes it a breeze for hackers to gain unauthorized access. Think about it—would you leave your front door unlocked just because it’s convenient? Probably not, and the same logic applies here.
Encryption Flaws
Encryption is crucial for protecting sensitive data during transmission. Unfortunately, not all VNC implementations come with robust encryption protocols. Some older versions of VNC use outdated encryption methods that can be easily cracked by sophisticated attackers.
Unpatched Software
Another common problem is the failure to keep VNC software up to date. Manufacturers frequently release patches to fix known vulnerabilities, but if you’re not applying these updates, you’re leaving yourself exposed to potential threats.
Read also:Town Spa Pizza Where Comfort Meets Flavor In Every Bite
Why Should You Care About Security Weakness in VNC?
Let’s break it down: VNC is often used to access sensitive information, such as financial records, personal data, and confidential business documents. If a hacker gains access to your VNC connection, they could steal this information, leading to identity theft, financial loss, or even corporate espionage.
And it’s not just about the data—hackers can also use compromised VNC connections as a gateway to attack other systems on your network. Once they’re in, it’s like they have free rein to do whatever they want. Scary stuff, right?
Real-World Examples of VNC Security Breaches
Don’t think this is just theoretical? Think again. There have been several high-profile cases of VNC security breaches that highlight the dangers of ignoring these vulnerabilities.
The 2019 VNC Breach
In 2019, researchers discovered thousands of unsecured VNC servers exposed on the internet. These servers were easily accessible without any authentication, allowing anyone to view and interact with the connected computers. Imagine walking into a bank and finding the vault wide open—crazy, right?
Targeted Attacks on Businesses
Businesses are prime targets for VNC-based attacks. Hackers often use VNC as a way to infiltrate corporate networks, stealing sensitive data and demanding ransomware payments. In one case, a major healthcare provider had to pay a hefty sum to regain control of their systems after a VNC-related breach.
Steps to Protect Yourself from Security Weakness in VNC
So, what can you do to safeguard your VNC connections? Here are some practical steps you can take to enhance your security:
Use Strong Passwords
This one’s a no-brainer. Use complex passwords that include a mix of uppercase and lowercase letters, numbers, and symbols. Avoid using easily guessable information, such as your name or birthdate.
Enable Encryption
Make sure your VNC software is configured to use strong encryption protocols, such as AES. This will help protect your data during transmission and make it much harder for attackers to intercept.
Keep Your Software Updated
Regularly check for updates to your VNC software and apply them as soon as they become available. Manufacturers release patches to fix known vulnerabilities, so staying up to date is crucial.
Advanced Security Measures for VNC
If you’re looking to take your VNC security to the next level, consider implementing some of these advanced measures:
Firewall Configuration
Configure your firewall to only allow VNC connections from trusted IP addresses. This will help prevent unauthorized access from unknown sources.
Two-Factor Authentication
Enable two-factor authentication (2FA) for an extra layer of security. Even if a hacker manages to guess your password, they’ll still need a second form of verification to gain access.
Network Segmentation
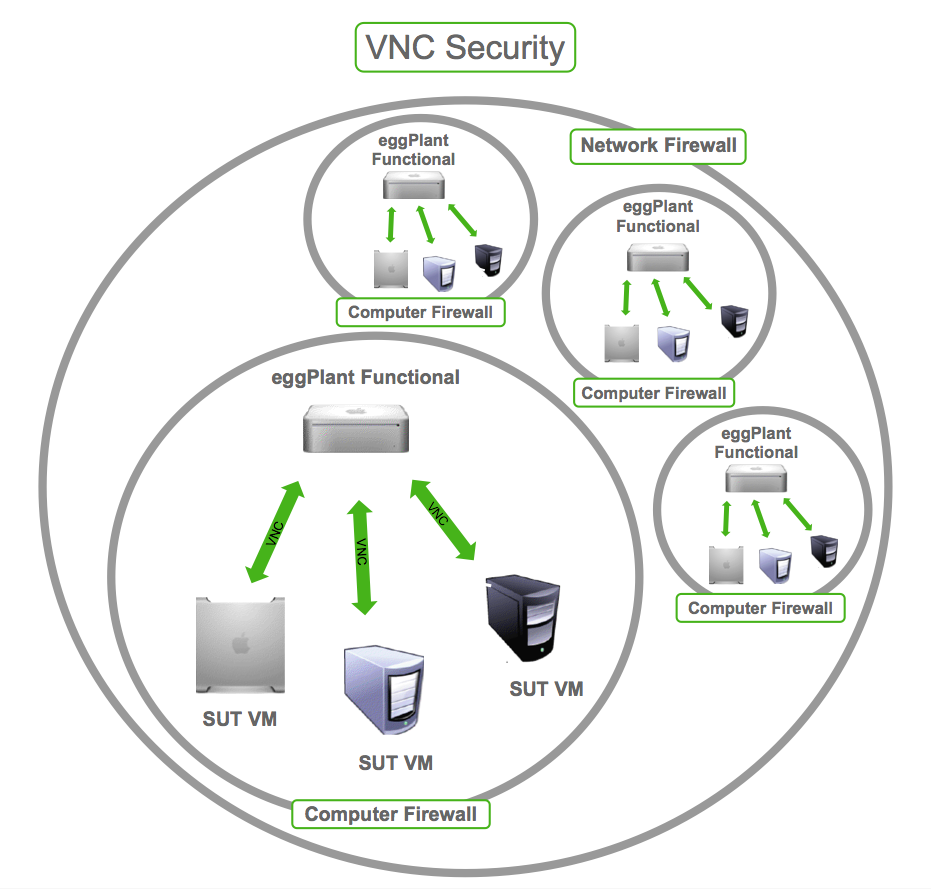
Segment your network to isolate VNC connections from other critical systems. This way, even if a hacker gains access to your VNC server, they won’t be able to move laterally across your network.
Tools to Detect VNC Security Weakness
There are several tools available that can help you detect and address VNC security weaknesses. Here are a few you might want to consider:
Shodan
Shodan is a search engine for internet-connected devices. You can use it to scan for unsecured VNC servers and identify potential vulnerabilities in your network.
Nmap
Nmap is a powerful network scanning tool that can help you identify open ports and services running on your network. Use it to check for exposed VNC connections and ensure they’re properly secured.
VNCScanner
VNCScanner is a specialized tool designed to scan for VNC servers and test their security configurations. It can help you identify weak passwords and other vulnerabilities before they’re exploited by attackers.
Future of VNC Security
As technology continues to evolve, so too will the methods used to secure VNC connections. Manufacturers are constantly working to improve encryption protocols, authentication mechanisms, and overall security features. However, it’s up to users to stay informed and take the necessary steps to protect themselves.
Conclusion
In conclusion, the security weakness in VNC is a real and pressing issue that shouldn’t be ignored. By understanding the common vulnerabilities and taking proactive steps to secure your connections, you can significantly reduce the risk of a breach.
So, what are you waiting for? Take action today and make sure your VNC connections are as secure as possible. And don’t forget to share this article with your friends and colleagues—it could save them from a potential disaster down the line.
Table of Contents
- Understanding VNC: The Basics
- Common Security Weakness in VNC
- Why Should You Care About Security Weakness in VNC?
- Real-World Examples of VNC Security Breaches
- Steps to Protect Yourself from Security Weakness in VNC
- Advanced Security Measures for VNC
- Tools to Detect VNC Security Weakness
- Future of VNC Security
- Conclusion
Article Recommendations